Understanding Tokens
If you’ve delved into the world of cryptocurrency and blockchain, you’ve likely encountered the terms “security tokens” and “utility tokens.” Though they may sound similar, they serve distinct purposes within the technological and financial ecosystems they’re part of. Let’s unravel what these tokens are all about and how they play pivotal roles in the digital world.
What is a Token? A token is a digital unit of account that resides on an existing blockchain, representing assets or utilities in various blockchain ecosystems.
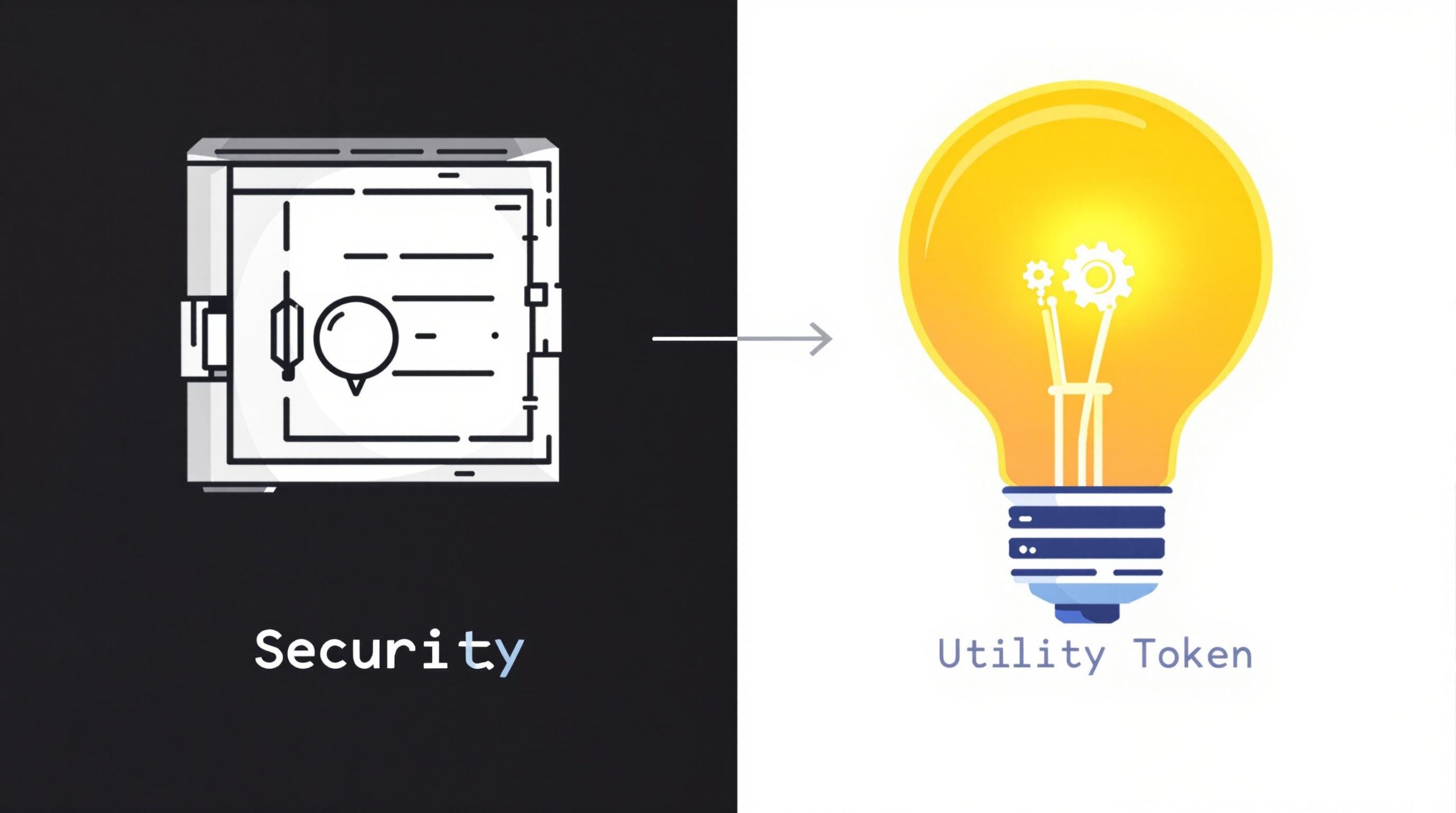
What Are Security Tokens?
Security tokens are digital contracts representing fractions of an asset, whether it’s equity, debt, real estate, or anything else with tangible value. They are typically subject to federal securities regulations just like traditional securities. By tokenizing an asset, security tokens offer the advantages of transparency, efficiency, and the ability to divide ownership into smaller units — a concept known as fractional ownership.
- Key Purpose: Security tokens are primarily used for investing in an asset, much like purchasing stock in a company where the token represents ownership rights.
- Regulatory Compliance: Unlike utility tokens, security tokens must adhere to regulatory frameworks, ensuring investor protection.
- Value Representation: These tokens reflect ownership in real-world assets, akin to having a digital share in a property or business.
How do Security Tokens Work? Security tokens function as digital representations of physical assets, complying with securities regulations to protect investors and offer ownership transparency.
The Role of Security Tokens
Security tokens aim to unlock liquidity in traditionally illiquid assets like real estate or collectibles. This is achieved by dividing assets into smaller portions that are easily tradable on token markets. Through platforms like Jara, investments in large infrastructure projects, such as the Lagos airport bond tokenization, become accessible to a global investor base.
“Jara – Unlocking the Future to Africa’s Crypto Ecosystem.” By leveraging security tokens, Jara is pioneering new ways for investors to engage with African infrastructure projects.
Challenges of Security Tokens
Despite their advantages, security tokens aren’t without challenges. The regulatory landscapes are complex and vary across jurisdictions, which may hinder cross-border transactions. Additionally, investors may face technical barriers to entry, requiring them to become familiar with digital wallets and blockchain technology. Another issue is market adoption; as a relatively new concept, widespread acceptance is still developing.
What Are Utility Tokens?
Utility tokens, unlike their security counterparts, are mainly used within a particular project’s ecosystem. They’re designed to provide users with access to services or products rather than an investment or ownership share. It’s like receiving a coupon that can be used for discounts or special perks on certain products or services within a blockchain platform.
- Key Purpose: Utility tokens are essential for interacting with the services or products of a platform, driving engagement rather than investment.
- Regulation: These tokens aren’t typically regulated as securities, allowing more flexibility in their usage.
- Access Focused: Utility tokens serve as a tool for accessing digital services or goods within their specific blockchain ecosystems.
What are Utility Tokens? Utility tokens provide access to a platform’s services, focusing on user engagement and are often distributed during ICOs for discount incentives.
The Role of Utility Tokens
Utility tokens play a crucial role in creating vibrant ecosystems on platforms. They serve as the medium through which users can engage with the offered services, like gaining special access or benefitting from discounts. Projects like Jara’s stablecoin-powered ecosystems can leverage utility tokens to foster community building and product utilization.
“Participate in the growth of a revolutionary platform.” Platforms like Jara empower users with utility tokens to enhance service interaction and loyalty.
Challenges of Utility Tokens
The flexibility of utility tokens comes with its own set of challenges. The market has seen instances of scams and insufficient regulatory oversight, leading to potential vulnerabilities for investors. Moreover, while they bypass some regulatory hurdles faced by security tokens, this lack of regulation can create an environment of uncertainty and risk, especially in less mature markets.
Despite these hurdles, utility tokens have shown immense potential in revolutionizing how services are accessed and used in the blockchain space, serving as the backbone of various decentralized applications.
Discover the power of digital access: Utility tokens revolutionize service engagement, offering unique opportunities for users within ecosystems such as Jara’s $JARA token infrastructure.
Understanding Security Tokens
Security tokens are digital assets that derive their value from an external, tradable asset, such as real estate or company shares. These tokens are subject to federal laws governing securities, ensuring investor protection.
“Compliance is not just an option—it’s a necessity. Security tokens are fundamentally intertwined with existing securities regulations.”
How Do Security Tokens Work?
Security tokens function by utilizing blockchain technology to digitally represent ownership in a real-world asset. For example, owning a security token might grant you a share in a company’s earnings, similar to traditional stock ownership.
- Token Creation: Security tokens are typically created during a Security Token Offering (STO), similar to an Initial Public Offering (IPO), but on the blockchain.
- Regulatory Compliance: They must comply with regulations like the Securities Act of 1933 and other SEC requirements, ensuring proper investor disclosures.
“Security tokens offer a fusion of traditional financial security and technological innovation.”
Exploring Utility Tokens
Utility tokens provide access to a specific product or service and are often used to fuel activities within a blockchain ecosystem. Unlike security tokens, they are not meant for investment purposes.
“Utility tokens are your digital ticket to unlocking exclusive blockchain features and services.”
Functionality of Utility Tokens
These tokens function as digital coupons or vouchers that users can redeem for services. They are not subject to securities regulations, making them easier and faster to distribute.
- Access Services: Utility tokens enable access to specific services on a blockchain platform, like cloud storage or bandwidth.
- Incentive Alignment: They align incentives between users and developers, fostering active ecosystem participation.
“Despite their flexibility, utility tokens must ensure they don’t inadvertently become securities under regulatory scrutiny.”
Comparing Security Tokens and Utility Tokens
Purpose and Usage
| Aspect | Security Tokens | Utility Tokens |
|---|---|---|
| Purpose | Investment and ownership in assets | Access to services within a platform |
| Regulation | Subject to federal securities laws | Not regulated as securities |
Rights and Benefits
- Security Tokens: Offer voting rights, dividends, and participation in profits.
- Utility Tokens: Provide discounted access or premium features without ownership rights.
“Choosing the right token depends on your needs—investment security or streamlined service access.”
Roles and Challenges
Security Tokens
- Role: Digitize ownership and facilitate investments in real-world assets.
- Challenges: Navigating complex securities laws and ensuring investor compliance.
Utility Tokens
- Role: Enhance user engagement by providing service access.
- Challenges: Risk of devaluation if the associated project fails or loses credibility.
“Both tokens offer unique opportunities but require careful planning and compliance to succeed.”
Real-World Examples
Security Tokens
- tZERO: A regulated platform that offers security tokens representing company stocks.
- Harbor: Real estate investment offerings through tokenized properties.
Utility Tokens
- Binance Coin (BNB): Used on the Binance exchange for transaction fee discounts.
- Basic Attention Token (BAT): Utilized in the Brave browser to enhance user and advertiser interactions.
Conclusion
Understanding the nuanced roles of security and utility tokens can help investors and developers make informed decisions aligned with their objectives. As blockchain technology continues to evolve, staying informed and compliant will be crucial in navigating this dynamic landscape.
“Navigate the crypto landscape with knowledge and strategy—choosing the right token is your first step.”

Security Tokens: Digital Securities for Modern Investments
Security tokens have emerged as a groundbreaking way to represent ownership in real-world assets on the blockchain. Imagine them as digitized shares of a company, but with the flexibility and transparency of blockchain technology. They’re not just a passing trend; they’re here to reshape how we think about investments.
“Security tokens open new avenues for investors, providing both transparency and regulatory compliance.” – At the core of digital asset innovation, security tokens deliver extensive trust and confidence.
How Security Tokens Work
Security tokens derive their value from external, tradeable assets like real estate or company shares. These tokens are subjected to rigorous financial regulations to ensure their legitimacy and protect investors. Simply put, if it passes the Howey Test, it’s likely a security token.
- Compliance: Must adhere to federal securities regulations, including the Securities Act of 1933 and Securities Exchange Act of 1934.
- Ownership: Represents ownership stake or entitlement to dividends and profits.
- Functionality: Offers potential voting rights, resembling traditional equity shares but in a digital form.
| Regulation | Details |
|---|---|
| Regulation D | Avoids registration by filing “Form D”; suitable for accredited investors. |
| Regulation A+ | Allows raising up to $50 million from non-accredited investors with SEC approval. |
| Regulation S | For offerings outside the USA, avoiding Section 5 of the 1933 Act but staying compliant with foreign laws. |
Did you know? Security tokens provide investors with an opportunity to own a piece of an asset digitally without the hassle of traditional paperwork.
Challenges Surrounding Security Tokens
Despite their innovative nature, security tokens face several hurdles. From navigating complex regulations to ensuring robust security measures against hacking, challenges abound. Here’s a quick look at some of the key issues:
- Regulatory Complexity: Staying compliant with varying global regulations demands significant expertise.
- Market Accessibility: Limited platforms and markets reduce liquidity options for these digital assets.
- Technological Risks: Smart contract vulnerabilities and cybersecurity threats pose ongoing risks.
Utility Tokens: Gateway to Blockchain Services
Unlike security tokens, utility tokens aren’t meant for investments. Instead, they grant access to a company’s product or service, acting like digital coupons for future use.
Understanding Utility Tokens
Think of utility tokens as tokens you earn at an arcade. They’re not for cashing out but for accessing rides and games. Similarly, utility tokens grant users access to specific applications within a blockchain network.
- Access: Primarily used to access a service or feature within a blockchain platform.
- Exemption: Often not subject to stringent securities regulations when correctly structured.
- Examples: Filecoin, Siacoin, Civic, and similar tokens provide service access rather than investment returns.
“With utility tokens, the line between user and stakeholder blurs, fostering community engagement and service adoption.” – This highlights their unique role in blockchain ecosystems.
Challenges & Concerns with Utility Tokens
Utility tokens also come with their set of challenges, largely stemming from the ICO boom of 2017, which saw a flood of token offerings with over-promised capabilities.
- Oversaturation: Excessive token offerings led to market saturation and user trust issues.
- Regulatory Ambiguity: Unregulated tokens run the risk of investor caution and legal challenges.
- Project Viability: Many projects faced reliability issues due to unrealistic goals and lack of real-world application.
Comparing Security Tokens and Utility Tokens
When navigating blockchain investments, understanding the differences between these tokens is crucial. Here’s a comparative overview of the two:
| Aspect | Security Token | Utility Token |
|---|---|---|
| Purpose | Investment | Service Access |
| Regulation | Strict (e.g., SEC Regulations) | Lesser or None |
| Rights | Ownership and Dividends | Service/Platform Use |
| Examples | Real estate-backed tokens | Filecoin, Civic |
“Choose the right token based on your goals: security for investment stability, utility for engagement and access.” – A tailored approach ensures alignment with your objectives.
The Evolving Landscape of Tokens
As blockchain technology continues to evolve, so does the nuanced ecosystem of digital tokens. Whether you’re leaning towards security tokens for their regulatory assurance or utility tokens for their functional accessibility, understanding each token’s unique benefits and limitations is key. How will you make your digital mark in this developing space?
Security Tokens vs. Utility Tokens: Unraveling the Differences
“Blockchain technology makes it possible to create a wide array of new business models.” – Elevate your understanding of tokens and their pivotal role in blockchain.
Understanding Tokens
In today’s tech-savvy world, you might have come across terms like tokens, coins, and cryptocurrency. While they might seem the same to many, each serves a unique purpose in the blockchain ecosystem. Let’s dive deeper into these terms, focusing mainly on security tokens and utility tokens.
What Are Security Tokens?
Security tokens are digital assets that derive value from an external, tradeable asset. These tokens represent ownership in assets like earnings streams, participation in underlying assets, or entitlements to dividends or interest payments.
- Key Concept: A security token is an investment asset backed by tangible entities like real estate or stocks.
- Legal Compliance: They must comply with federal security regulations to avoid legal consequences.
- Functionality: Security tokens often give holders ownership rights and a stake in company decisions.
Security Token Offerings (STOs) enhance investor trust by linking digital tokens to secure investments.
Regulation Compliance for Security Tokens
Security tokens are subject to rigorous regulations similar to traditional securities.
- Regulation D: Allows offerings without SEC registration post-filing of “Form D”.
- Regulation A+: Permits offerings to non-accredited investors with a cap of $50 million.
- Regulation S: Applies to offerings outside the US, invoking the local nation’s security laws.
Security Tokens’ Roles
Security tokens offer a digitized representation of ownership while adhering to strict regulatory frameworks. This ensures transparency, security, and investor trust.
By passing the Howey Test, a cryptocurrency is classified as a security token, needing to follow federal securities regulations.
Challenges Facing Security Tokens
Despite their advantages, security tokens face several challenges:
- Regulatory Hurdles: Constantly evolving local and global laws.
- Market Acceptance: Ensuring wide adoption amidst skepticism.
What Are Utility Tokens?
Utility tokens, often referred to as app coins, provide users access to a specific product or service within a blockchain network.
- Key Concept: Unlike security tokens, utility tokens offer access, not investment returns.
- Regulatory Exemption: If structured correctly, utility tokens can be exempt from securities laws.
How Does a Utility Token Work?
The primary function of utility tokens is to grant access or rights related to specific services, often acting as digital coupons for future service or product discounts.
Roles of Utility Tokens
- Service Access: Provides users with access to services or products in a blockchain.
- Project Financing: Used as a funding mechanism during ICOs.
Utility Token Issues and Challenges
The utility token market exploded during the ICO craze of 2017, but with it came numerous challenges:
- Lack of Regulation: Often leads to investor skepticism.
- Market Volatility: Prone to rapid price changes.
Security Tokens vs Utility Tokens
To understand the stark differences:
| Aspect | Security Tokens | Utility Tokens |
|---|---|---|
| Purpose | Investment and ownership | Access and utility |
| Regulation | Strictly regulated under security laws | Not typically subject to securities regulations |
| Rights and Benefits | Dividends and voting rights | Access to services/products |
| Underlying Asset | Linked to tangible assets | No direct asset backing |
Security Tokens offer a compliant investment path, akin to traditional financial assets, whereas Utility Tokens provide participatory functions in a blockchain network.
Real Life Examples
Security Tokens
- SPiCE VC: Offers venture capital investment through digital shares.
- tZERO: Provides a blockchain platform for trading security tokens.
Utility Tokens
- Filecoin: Decentralized storage network incentivizing data provisioning.
- Siacoin: Facilitates decentralized cloud storage.
Navigating the Future of Tokens
As blockchain technology evolves, both security and utility tokens will continue to drive innovation. Investors and developers should remain informed of regulatory changes and project their strategies accordingly.
“Stay versed with the flux of blockchain regulations to harness potential opportunities.” – Use this knowledge to strategically navigate the crypto-token landscape.
Frequently Asked Questions
- What is a security token? A digital asset representing ownership or investment in a tangible asset.
- What is a utility token? A token used primarily to access services or products within a blockchain ecosystem.
- Examples of a utility token? Filecoin, Siacoin.
- Examples of a security token? SPiCE VC, tZERO.
“Your participation fuels the future of digital innovation.” – Embrace the change brought by tokens and stay ahead in the blockchain realm.

Related Articles
Delve deeper into the fascinating world of tokenization with our curated list of articles.

Join the Jara Revolution Today!
Your journey into the world of tokenization starts with Jara. Dive into the future of finance by downloading the Jara Wallet App today!
Explore the dynamic universe of security tokens and utility tokens with Jara’s cutting-edge solutions. Our platform brings the power of global capital to African assets, making it easier to invest in transformative opportunities.
Ready to make a difference? Download the Jara Wallet App now on your Android or iPhone device to begin your journey.
Stay connected and informed by following us on social media. Join our community to keep up with the latest advancements and take an active role in shaping the future of tokenization.
Understanding Personal Injury Law
- Definition of Personal Injury Law: Explanation of what constitutes personal injury law.
- Common Types of Personal Injury Cases: Overview of cases such as car accidents, slip and falls, and medical malpractice.
- Legal Rights of Personal Injury Victims: Description of the rights entitled to victims under law.
How to Choose a Personal Injury Lawyer
- Researching Lawyer Qualifications: Importance of verifying credentials and experience.
- Checking Client Testimonials: How client reviews can offer insight into a lawyer’s effectiveness.
- Initial Consultation Questions: Key questions to ask during the first meeting with a lawyer.
The Personal Injury Claim Process
- Step 1: Initial Consultation: Detailed look at the first meeting with a lawyer.
- Step 2: Investigation and Evidence Gathering: Process of collecting necessary documents and statements.
- Step 3: Negotiation and Settlement: Explanation of how settlement discussions work.
- Step 4: Trial Proceeding: What happens if the case goes to trial.
Common Challenges in Personal Injury Cases
- Dealing with Insurance Companies: Challenges posed by insurance adjusters and tactics they use.
- Lack of Evidence: How insufficient evidence can impact a case.
- Understanding Legal Jargon: Making sense of complex legal terms and processes.
Benefits of Hiring a Personal Injury Lawyer
- Expertise in Legal Procedures: How a lawyer’s experience can streamline the process.
- Maximizing Compensation: Strategies attorneys use to ensure fair compensation.
- Stress Reduction: How legal representation alleviates the burden of navigating a claim.
“Your Voice, Our Mission” – we champion your rights with the tenacity and dedication that has earned us the trust of our community members.